Not all electronic and digital signatures are the same. In this blog, we discuss choosing the right eSignature for your business.
At a basic level, users can use any mark on an electronic document to capture the signer’s intent to approve or accept the contents. The form of the “mark” or how it was created is not important. What is important is proving who made the mark and that no one made any changes subsequently.

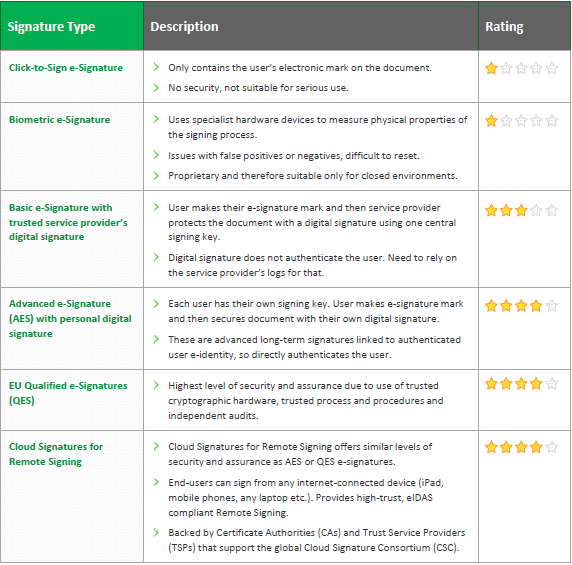
What are the different signature types?
- Click-to-sign signatures
- Biometric eSignatures
- Basic electronic signatures
- Advanced Electronic Signatures (AES)
- EU Qualified Electronic Signatures (QES)
- Cloud signatures for remote signing
What is a Click-to-Sign signature?
A Click-to-Sign eSignature can be any mark placed on a document to indicate the signer’s consent. A mark could be a mouse squiggle, a signature drawn on a touch screen, an uploaded image, a tick box, a signature typed in a special script font, a typed name or even an email address.
These electronic marks can be easily copied from one document to another. They don’t provide cryptographic protection, allowing anyone to change the document once a mark has been applied. Click-to-sign signatures can also be easily repudiated, as a signer can claim, “that’s not my signature”.
Although most jurisdictions will admit a ‘click-to-sign’ e-signature in a court of law as evidence, they don’t provide any conclusive evidence and can be easily disputed. When choosing the right eSignature, it's important to consider whether it could ever be required as evidence in a court of law.
What is a biometric electronic signature?
A biometric eSignature is created using biometric information unique to the user and attached to the document.
Biometric information can include fingerprints, iris scans or the most common example is the physical aspects of a user’s signature drawing process using a specialist tablet and stylus. Measurements include the speed, pressure, pen incline, shape and size of the signature.
Biometric eSignatures are susceptible to spoofing through replay attacks and the signing devices themselves can also be hacked.
Biometric eSignatures are effectively complex passwords that are difficult to reset. There are also challenges with verifying and storing biometric data and are often false-positive and false-negative results from the mechanism.
Like ‘click-to-sign’ signatures, biometric eSignatures are accepted in court, but weak security and interoperability mean they do not provide convincing evidential proof.
What is a basic electronic signature?
When choosing the right eSignature for your business that doesn't require cryptographic legality - you may consider basic eSignatures. Basic electronic signatures are defined under the eIDAS regulation as:
- Immediate signing, no user registration or login required
- Document signed and protected with server held signing key or eSeal only
- May or may not include a trusted timestamp
- The signer’s identity is not verifiable directly from the signed document
A cryptographic digital signature is created using a server-held signing key or an eSeal for organisations. The key belongs to the trusted service provider’s (TSP) organisation.
When the user applies the eSignature mark, a digital signature is attached. This process cryptographically binds the mark to the document, protecting the document from any subsequent changes to ensure data integrity. Esignature software can add a timestamp to record the date and time the user signed.
Basic eSignatures cannot identify a signer as the digital signature by itself doesn’t authenticate the user. This is because basic eSignatures rely on the service provider’s logs. In some cases, access to signature logs isn’t possible once the user is no longer a customer of the service provider or the organisation goes out of business.
Is an electronic signature as legal as a paper signature?
Basic signatures are accepted in court. Logs will need to be provided as evidence, but as mentioned, it’s not always possible to access these from the service provider. If a timestamp has been used, its integrity will depend on how it was generated – timestamps taken from a computer clock can be manipulated.
Basic eSignatures protected with a standard digital signature such as PAdES are recognised and implemented in many third-party PDF document readers such as Adobe® Acrobat Reader DC.
Users can set up the basic eSignature to protect the document for long-term validation (LTV). A PAdES LTA signature type (for the digital signature/seal component) can protect the document from any unauthorised changes.
However, since the signature doesn’t contain robust user authentication information, the basic eSignature loses its advantage in interoperability.
Conclusion
When choosing the right eSignature for your business, we recommend the basic electronic signature as an entry-level eSignature scheme.
It provides reasonable Levels of Assurance - as long as the service provider’s processes and procedures around authenticating users and managing associated logs are secure. Security is strengthened when the user is authenticated using single or multi-factor authentication, identified in the ‘reason for signing field’, and when a long-term digital signature from the service provider is used to provide LTV.
In this series’ next blog, we’ll discuss the difference between Advanced Electronic Signatures (AES) and Qualified Electronic Signatures (QES).
Want to learn more about the different types of eSignatures and which suits your business needs? Download our Choosing the Right Type of eSignature eBook.
Comparison of different types of e-signatures